by Tore Maras
Election Concerns Courts Evaded, the Left Discredited, MAGA Networks Silenced—ODNI Stepped In
True justice never arrives in a Ferrari, it rides on a donkey.
When federal agents seized election equipment in Fulton County, most commentary fixated on optics—who was present, who authorized it, and what it “looked like” politically. But one detail cut through the noise: the presence of the Office of the Director of National Intelligence. That alone should have ended the speculation. ODNI does not appear for show, and it does not appear for routine disputes. When it appears, it is because something has crossed a threshold—from local controversy into national-security exposure.
What followed was predictable. Instead of asking why intelligence containment was necessary, public debate raced to minimize the question itself.
The panic over the ODNI’s presence at the Fulton County raid misses the point entirely.
The Office of the Director of National Intelligence was not created to kick down doors, run investigations, or replace law enforcement. It was created because the United States learned—catastrophically—that intelligence trapped in silos is worse than intelligence not collected at all.
ODNI was established by the Intelligence Reform and Terrorism Prevention Act of 2004 in direct response to the failures preceding 9/11. The intelligence existed. The warnings existed. What did not exist was a mechanism to force coordination, integrate information across agencies, and control access once sensitive material crossed institutional boundaries. The 9/11 Commission exposed that failure. Congress acted. ODNI was designed not to operate in the field, but to oversee, synchronize, and compartmentalize intelligence across the federal government.
The Director of National Intelligence serves as the President’s principal intelligence advisor and oversees the entire Intelligence Community. That oversight is strategic, not operational. The DNI does not conduct raids or run criminal cases. Intelligence agencies remain under their parent departments by design: CIA operates independently, NSA and DIA sit under Defense, and the FBI’s intelligence arm remains under Justice. ODNI exists above operations, not inside them.
Which is precisely why its presence at a local raid should raise a different and far more serious question.
ODNI does not appear for routine law enforcement activity. It appears when intelligence equities are at risk—when seized material may implicate foreign access, classified vulnerabilities, sensitive technical architectures, or previously assessed threat vectors that cannot be freely disseminated without consequence.
This is not speculation. It is ODNI’s statutory role.
Public statements have cited the DNI’s responsibility for identifying vulnerabilities in critical infrastructure and protecting against exploitation, including in electronic voting systems, under 50 U.S.C. § 3371d. Online critics have seized on the absence of a publicly named foreign adversary to argue that ODNI’s involvement was unjustified. That argument misunderstands how intelligence oversight actually works.
Foreign interference does not need to announce itself as a discrete attack—Russia here, China there—before intelligence authorities act. Intelligence action is triggered by exposure pathways, not by completed attribution.
My AFFIDAVIT documents those exposure pathways in detail.
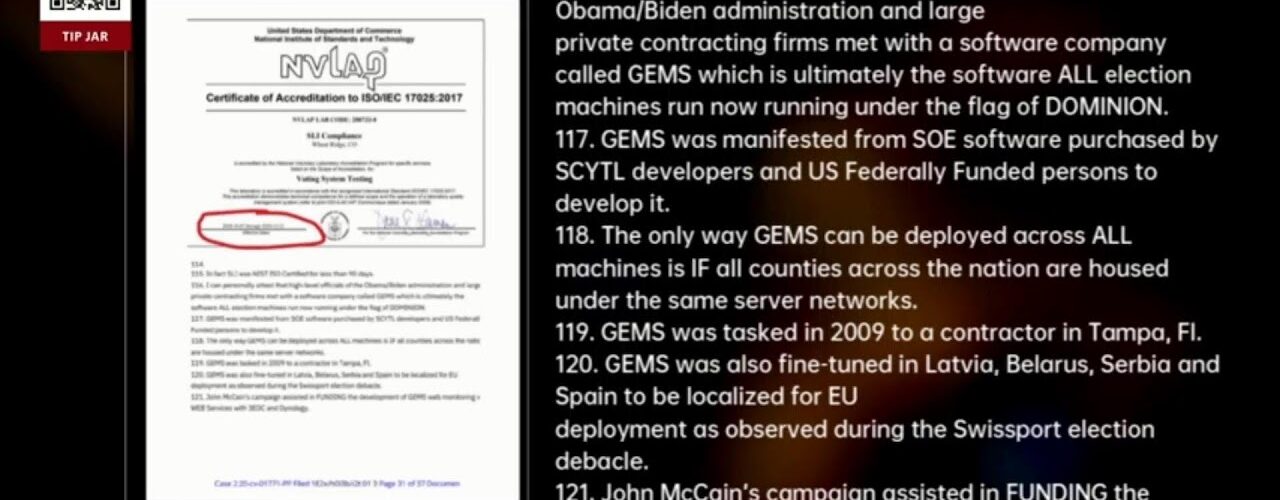
It establishes that election systems relied on commercial off-the-shelf hardware sourced from foreign manufacturers, with firmware and software update chains that were not continuously examined by properly accredited Voting System Test Laboratories. That alone creates a counterintelligence concern. Persistent hardware-level exposure does not require a named adversary. It requires risk.
The AFFIDAVIT further documents that election-related data and reporting infrastructure transited foreign-hosted environments through international content delivery networks, including Akamai Technologies, with infrastructure located outside the United States and corporate ties extending into jurisdictions of intelligence concern. At that point, the issue is no longer “foreign disinformation” in the social-media sense. It is foreign infrastructure touching U.S. critical systems.
That falls squarely within ODNI’s remit.
Critics point to the absence of public warnings to Congress or intelligence committees as proof that no foreign nexus exists. That argument collapses under a basic understanding of compartmentalization. My AFFIDAVIT explains why certain findings cannot be freely disclosed. Cryptographic architectures employing mixing, shuffling, and trapdoor commitments eliminate universal verifiability and obscure manipulation pathways by design. Broadcasting preliminary assessments in such systems risks exposing sources, methods, and vulnerabilities that themselves become exploitable.
The claim that this is a purely domestic matter fails for another reason: regulatory collapse.
Under the Help America Vote Act, the Election Assistance Commission is required to ensure that voting systems are tested by properly accredited laboratories. My affidavit demonstrates that this did not occur. Independent Verification and Validation was performed by entities lacking valid EAC accreditation or relying on NIST certifications that do not satisfy HAVA requirements. Certification is not procedural trivia. It is the firewall between domestic control and foreign exposure. When it fails, foreign-sourced components and foreign-assisted architectures enter systems without federally mandated safeguards.
Once domestic regulators permit that exposure, the risk is no longer domestic. It is structural.
Arguments that ODNI’s presence was unnecessary because DOJ did not request it misunderstand ODNI’s function. ODNI does not deploy at the invitation of prosecutors when intelligence equities are implicated. It deploys to manage custody, access, and dissemination when seized material may intersect with classified threat assessments that law enforcement is neither cleared nor structured to handle.
Historical comparisons to other raids miss the point entirely. Those cases involved discrete criminal statutes. This matter involves critical infrastructure, foreign dependencies, cryptographic opacity, and certification failure. Different risk profile. Different playbook.
Intelligence oversight does not wait for certainty. It responds to exposure.
My AFFIDAVIT does not need to prove that a foreign government altered votes to justify ODNI involvement. It demonstrates that foreign access, foreign infrastructure, and foreign-assisted system design were present in systems that cannot mathematically prove their own integrity. That is more than sufficient.
When equipment, servers, or logs are seized under those conditions, ODNI’s role is not symbolic. It is custodial. Who accesses the material. Who images it. Who analyzes it. What remains compartmentalized. What can be shared. What cannot. This is about preventing intelligence spillage before it becomes a national-security breach.
Elections are designated critical infrastructure. Once there is a credible possibility that foreign entities have accessed, influenced, or embedded themselves into those systems, the issue ceases to be administrative or criminal alone. It becomes strategic.
That is where my AFFIDAVIT begins—not as accusation, but as documentation. And that is why ODNI’s presence was not extraordinary.
It was inevitable.
Why intelligence containment became necessary
At this point, the question is no longer why ODNI was present. The question is why intelligence containment became necessary at all.
The answer lies squarely with the Election Assistance Commission.
Under the Help America Vote Act of 2002, the EAC is not an advisory body. It is a gatekeeper. Congress explicitly tasked it with ensuring that voting systems are tested, certified, and validated by properly accredited laboratories capable of examining both software and hardware against federal standards. This was not optional. It was designed to prevent exactly the kind of foreign exposure now under discussion.
My AFFIDAVIT documents that this safeguard failed.
Independent Verification and Validation was conducted by entities that lacked valid EAC accreditation at the time testing occurred, or relied on NIST certifications that do not satisfy HAVA’s statutory requirements. This is not a technicality. NIST’s role is advisory and standards-based. EAC accreditation is the legal mechanism that ensures those standards are actually enforced. Substituting one for the other is not compliance. It is circumvention.
That failure had cascading consequences.
Without properly accredited testing, commercial off-the-shelf hardware entered election systems without rigorous examination at the firmware and hardware layers. These components are not static. They receive frequent updates, often sourced from foreign manufacturers, creating persistent access points that software audits cannot detect. Certification exists precisely to prevent invisible exposure at that layer. When certification fails, foreign dependency is no longer hypothetical. It is embedded.
The EAC’s failure also meant that software architectures with known integrity limitations—systems that eliminate universal verifiability through cryptographic mixing, shuffling, and trapdoor commitments—were allowed to operate without meaningful external assurance. These designs do not merely complicate audits. They prevent proof. Once deployed at scale, they create systems whose integrity cannot be conclusively demonstrated, even after the fact.
From an intelligence perspective, that is not an election administration problem. It is a systemic assurance failure.
The moment foreign-sourced components, foreign-hosted infrastructure, and unverifiable system architectures converge under federal regulatory neglect, the risk profile changes. What should have been prevented at the certification stage becomes something that must be contained after the fact. That is where intelligence oversight enters—not to assign blame, but to prevent further exposure.
This is the consequence critics refuse to grapple with. Intelligence containment is not an accusation. It is damage control.
Once systems designated as critical infrastructure are found to have operated outside federally mandated safeguards, every component becomes potentially sensitive. Hardware may reveal access pathways. Logs may expose routing patterns. Configuration files may intersect with vulnerabilities already identified in classified reporting. At that point, routine evidentiary handling is no longer safe.
ODNI’s role becomes unavoidable.
The presence of ODNI at Fulton County was not a reaction to public controversy. It was the downstream effect of regulatory failure. The EAC’s inability—or unwillingness—to enforce HAVA standards created a situation where election systems were exposed in ways that could not be undone by audits, recounts, or court rulings. Once those systems were seized, intelligence containment was the only responsible course of action.
This is why the narrative framing this as bureaucratic overreach is backward. The overreach occurred when statutory safeguards were ignored. The intelligence response followed because the damage was already done.
Accountability, therefore, does not begin with ODNI. It begins with the regulatory failure that made ODNI necessary. And until that failure is confronted honestly, every discussion about election integrity will remain trapped in surface-level arguments, while the structural risk goes unaddressed.
That is the context in which my AFFIDAVIT exists—not to inflame, but to document how a preventable regulatory collapse escalated into a national-security concern.
And once that escalation occurred, containment was no longer optional.
ELECTION CONCERNS
None of this is to suggest that domestic election issues do not exist. Ballot harvesting, unlawful voting, chain-of-custody violations, and administrative misconduct are real concerns. They are tangible. They are observable. They are legally addressable through audits, prosecutions, legislative reform, and enforcement. Domestic problems, however serious, remain within domestic control. They can be investigated, corrected, and prevented through ordinary democratic mechanisms.
Foreign access is different.
Foreign access is not a question of individual misconduct. It is a question of system integrity. Once foreign entities gain visibility into, influence over, or architectural presence within critical election infrastructure, the problem is no longer about counting ballots correctly. It is about whether the system itself can be trusted to prove its own legitimacy.
That is the line this debate keeps refusing to acknowledge.
Domestic election violations can be unwound. Foreign exposure cannot simply be “fixed” after the fact. Hardware dependencies, firmware pathways, foreign-hosted infrastructure, and cryptographic systems that defeat verifiability do not announce themselves. They persist quietly, across election cycles, jurisdictions, and administrations. They are not corrected by recounts or court rulings. They are contained—or they metastasize.
This is why intelligence agencies focus on exposure rather than outcome. And it is why the presence of ODNI matters far more than any individual allegation of fraud. Intelligence oversight is not about relitigating elections. It is about protecting the legitimacy of the state itself by ensuring that foreign access does not become an invisible, permanent feature of democratic systems.
My affidavit does not argue that foreign access is the only problem. It demonstrates that it is the most consequential one. Domestic violations undermine confidence. Foreign access undermines sovereignty.
One can be prosecuted. The other must be prevented.
And that distinction—between what can be corrected internally and what must be contained at the national-security level—is the distinction that explains everything that followed
WHY PEOPLE PRETEND MY AFFIDAVIT DOESN’T EXIST
What my affidavit did—powerfully and deliberately—is establish credible, technical, and documented grounds showing that U.S. election systems were exposed to foreign access and structural manipulation pathways, and that this exposure rises to the level of a national-security concern rather than a conventional election dispute.
That distinction matters enormously.
Courts require proof of a completed act tied to a justiciable remedy: who did what, when, with what intent, and how the court can fix it. My affidavit operates at a different level. It demonstrates that the systems in question were architected, certified, deployed, and operated in ways that cannot reliably prove their own integrity, while intersecting with foreign supply chains, foreign infrastructure, and foreign-assisted software lineages. That is not a claim of outcome manipulation. It is a claim of assurance collapse.
From an intelligence and national-security perspective, that is the crux.
I did not argue, “Here is definitive proof that votes were changed on a specific date.” I argued something far more destabilizing to the status quo: that the United States adopted election technologies and governance structures that mirror tools used abroad in democracy-promotion and influence operations—sometimes funded or supported by U.S. entities themselves—and that once those systems are domestically deployed without enforceable verifiability, the distinction between internal administration and external interference collapses.
That is why my affidavit occupies such an uncomfortable institutional space.
If a court were to squarely address my claims, it would be forced to confront questions it is not designed to answer: whether election systems constitute critical infrastructure vulnerabilities; whether foreign access without attribution is itself disqualifying; whether regulatory failure transformed a civic process into an intelligence exposure; and whether legitimacy can be legally presumed when systems cannot mathematically demonstrate integrity. These are not evidentiary questions. They are sovereignty questions.
ODNI and Interest in my AFFIDAVIT
Every court that had my affidavit – skipped it. Quite literally, skipped over it.Courts did not avoid my affidavit because it was incoherent or irrelevant. They avoided it because it fundamentally recharacterized the dispute. I was not asking the court to resolve a conventional election challenge. I was asserting that the systems themselves—by design, architecture, and foreign exposure—constitute a national-security risk that sits outside ordinary judicial remedies.
That matters.
Courts are structurally ill-equipped to adjudicate intelligence exposure. Once a claim crosses from “Was this law violated?” into “Does this system expose the United States to foreign exploitation?”, the judiciary loses its footing. That terrain implicates classified assessments, executive authority, and the political-question doctrine. Judges do not have discovery tools for intelligence equities, nor do they have jurisdiction to compel disclosure of sources and methods. The safest institutional response is avoidance.
That is what Sidney Powell encountered.
When I testified that these systems function as strategic tools—used abroad under democracy-promotion frameworks, funded through U.S. programs, and deployed in post-conflict or transitional states—I was not making a moral accusation. I was describing a documented foreign-policy pattern. Election technology has been used internationally as part of state-building, influence operations, and legitimacy engineering. Ukraine during Maidan is one example. My affidavit traces funding pathways, software lineage, and institutional continuity consistent with that history.
Where courts recoil is when that history is brought home.
Describing these systems as “weapons of mass destruction” is conceptually accurate but categorically incompatible with legal forums. Courts hear “WMD” as statutory language tied to kinetic harm. What I was actually describing—and what intelligence agencies understand—is something closer to weapons of mass influence: strategic systems capable of legitimacy disruption at scale. Those are instruments of national power. They are not courtroom exhibits.
That distinction explains the silence.
Judges can rule on ballot access. They can rule on chain of custody. They can rule on statutory compliance. They cannot rule on whether the United States has deployed, reused, or inherited systems that—intentionally or not—mirror influence architectures used overseas. That question implicates the executive branch, intelligence oversight, and foreign-policy continuity across administrations.
So the courts sidestepped—not because my affidavit was weak, but because it was too strong in the wrong jurisdiction.
My affidavit effectively said this is not about fraud; it is about sovereignty. It is not about one election; it is about systemic exposure. It is not about criminal intent; it is about architecture that eliminates verifiability while intersecting foreign infrastructure and foreign-assisted design. That reframes a legal case into a national-security briefing.
And when that happens, courts do not refute. They decline.
What followed was equally instructive.
A broad constellation of influence networks—commentators, advocacy groups, credentialed “experts,” and aligned media voices—moved aggressively to discredit me and dismiss the affidavit. Not by engaging its core claims, but by redirecting attention to domestic election issues: ballot harvesting, illegal voting, administrative error, chain-of-custody disputes. Issues that are tangible, politically familiar, and—critically—optically resolvable. Those arguments allow the system to say, “We looked. We fixed it. Move on.”
My affidavit does not allow that.
It frames the issue as one that cannot be explained away with optics. You cannot claim an election is secure, sovereign, or resolved when the underlying systems cannot mathematically prove their own integrity and simultaneously intersect foreign supply chains, foreign infrastructure, and foreign-assisted software lineages. That is a critical-infrastructure problem. And critical-infrastructure problems trigger national-security scrutiny whether anyone is comfortable with that or not.
That is why the response focused on discrediting the messenger rather than addressing the message.
Which raises an unavoidable question—not as an accusation, but as a matter of logic: when coordinated influence networks mobilize to steer attention away from foreign exposure and toward domestically containable narratives, who benefits? Cloaking funding sources, laundering advocacy through NGOs, and obscuring financial origins are well-documented practices. Whether these actors are knowingly aligned, structurally incentivized, or simply operating within narratives they do not fully understand is an open question.
Unwillingly vs willingly? Unknowingly vs Knowingly?
What deserves scrutiny is not disagreement over conclusions, but the pattern of response. A broad network of voices moved in near unison to redirect attention away from foreign exposure and toward domestically containable explanations. The question, then, is not whether these actors disagree with my affidavit. It is whether they understand what it actually asserts—and if they do, why they refuse to engage its core claim.
Are these networks acting unknowingly, constrained by narratives they never examine? Are they structurally incentivized to avoid questions that implicate national security rather than partisan blame? Or are they knowingly steering public attention away from foreign exposure because doing so preserves institutional stability, funding streams, or access?
The answer may vary by actor. But the effect is uniform: the central issue is never addressed.
That issue is not fraud in the retail sense. It is whether critical infrastructure systems were allowed to operate outside enforceable safeguards while intersecting foreign supply chains, foreign infrastructure, and unverifiable architectures. That is not a matter of opinion. It is a matter of record.
And it is precisely why the response focused on discrediting the affiant rather than confronting what it documents.
But one thing is clear: their arguments never confront the core claim.
And that is the point.
Once an issue is framed as national-security exposure rather than a domestic election dispute, intelligence containment replaces judicial resolution. That is why ODNI appears. That is why certification failure matters more than individual misconduct. And that is why my affidavit was never meaningfully engaged on the merits—it addressed risks the courts were neither equipped nor authorized to resolve.
The avoidance was not accidental. It was structural.
ODNI and other official agencies never referenced my affidavit when engaging media or influence networks—and that omission is telling. Whether intentional or strategic, it left space to observe which networks would dismiss the issue outright, which would redirect attention to safer domestic narratives, and which would amplify distortions. In intelligence terms, that silence functions as a filter: revealing who may be knowingly aligned with foreign interests, who is structurally incentivized, who is simply repeating hired talking points, and who is operating without understanding at all.
The affidavit didn’t need defending. ODNI’s silence let the networks expose themselves. ~Terpsehore Maras
There is a Solution
This is where the conversation must finally move forward.
Sovereignty does not fail all at once. It erodes when systems are optimized for speed and efficiency at the expense of accuracy, when statutory safeguards are treated as optional, and when regulatory bodies charged with enforcement fail to do their jobs. My affidavit documents how that erosion occurs—not through spectacle, but through architecture, procurement decisions, and regulatory neglect.
For years, electronic election systems have been justified as cost-saving and efficient. In reality, they have done the opposite. To save taxpayer dollars in the short term, we expanded the threat surface of the most critical civic function we have. We introduced complex hardware, opaque software, foreign supply chains, continuous update requirements, and unverifiable cryptographic processes into systems that should have been simple, transparent, and provable. The result is not efficiency—it is permanent uncertainty and recurring intelligence containment.
Accuracy is not a luxury. It is the foundation of legitimacy.
Until the Help America Vote Act is enforced as written—until accreditation is real, hardware is examined at the level it was designed to be examined, and foreign exposure is treated as disqualifying rather than inconvenient—every election will carry the same unresolved risk. And with that risk comes the same outcome: intelligence agencies stepping in after the fact to manage exposure that should never have existed in the first place.
There is a straightforward solution that does not require new technology, new funding streams, or new authorities. It requires discipline.
Paper ballots. Hand counted. Publicly observable. Auditable without encryption keys, proprietary software, or foreign infrastructure. Slower, yes—but accurate. Boring, yes—but sovereign. Elections are not a business process to be optimized. They are a legitimacy process to be protected.
ODNI’s presence should not be normalized. It should be understood as a warning.
If intelligence agencies are required to secure election materials after the fact, then the failure occurred long before Election Day. The remedy is not more secrecy, more automation, or more narrative management. The remedy is restoring systems that can prove their own integrity without intelligence oversight.
Until we choose accuracy over efficiency, and sovereignty over convenience, the question is not whether ODNI will return.
The question is why we keep building systems that require them to.
🐦⬛
If you like Tore’s work, you can tip or support her via TIP ME or subscribe to her on Subscribestar! You can also follow and subscribe to her on Rumble and Locals or subscribe to her Substack. www.toresays.com